#Metasploit tutorial
Explore tagged Tumblr posts
Text
Comment Exploiter les Vulnérabilités Avancées avec Metasploit ?
Metasploit est un outil puissant de test d’intrusion qui permet d’identifier, d’exploiter et de compromettre des systèmes vulnérables. Il offre une large gamme de modules pour mener des attaques de type exploit, créer des payloads personnalisés et post-exploiter les cibles. C’est une plateforme indispensable pour les hackers éthiques et les professionnels de la sécurité. 🔐 Modules Principaux…
#cybersécurité#exploitation avancée Metasploit#exploitation de vulnérabilités#Metasploit tutorial#payload Metasploit#post-exploitation#protection contre Metasploit#test d&039;intrusion
0 notes
Video
youtube
HackTheBox Granny root WriteUp metasploit tutorial IIS 6.0 and local_exp...
0 notes
Video
youtube
Ethical Hacking Tutorials 35 Acquiring Metasploit
0 notes
Text
Unleashing Python's Potential: A Comprehensive Guide to Python in Modern Cybersecurity
Introduction: Unlocking the Power of Python in Cybersecurity
In today's rapidly evolving cybersecurity landscape, Python stands out as a versatile and indispensable tool for professionals seeking to fortify digital defenses against a myriad of threats. With its intuitive syntax, extensive library ecosystem, and powerful scripting capabilities, Python continues to revolutionize the way cybersecurity tasks are performed.
Considering the kind support of Learn Python Course in Hyderabad, Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

This comprehensive guide explores Python's pivotal role in cybersecurity, shedding light on its diverse applications and benefits.
1. Versatility Redefined: Python's Role in Cybersecurity
Python has redefined the concept of versatility in the realm of cybersecurity. Its user-friendly syntax and extensive library support empower professionals to address a wide range of security challenges, from network monitoring to threat detection and incident response. Python's adaptability makes it a go-to choice for cybersecurity practitioners seeking effective and efficient solutions.
2. Harnessing the Power of Libraries and Frameworks
In the arsenal of cybersecurity professionals, Python's extensive library ecosystem shines brightly. From packet manipulation to cryptographic operations and web scraping, Python libraries such as Scapy, Crypto, and Beautiful Soup provide essential building blocks for developing robust security solutions. Additionally, frameworks like Django and Flask streamline the process of building secure web applications, reinforcing Python's position as a cornerstone of modern cybersecurity.
3. Automating Security Operations with Python Scripts
Python's scripting capabilities are a game-changer in the realm of security operations. Security analysts leverage Python scripts to automate repetitive tasks, accelerate incident response, and enhance overall operational efficiency. Whether it's parsing log files, conducting vulnerability scans, or orchestrating complex security workflows, Python scripts empower professionals to tackle cybersecurity challenges with precision and agility.
4. Platform-Agnostic Solutions for Cross-Platform Security
One of Python's standout features is its platform-agnostic nature, allowing security professionals to develop solutions that seamlessly run across diverse operating systems and environments. This cross-platform compatibility ensures that security tools and scripts built in Python can be deployed across various systems with minimal modifications, facilitating collaboration and interoperability in cybersecurity operations. Enrolling in the Best Python Certification Online can help people realise Python's full potential and gain a deeper understanding of its complexities.
5. Community Collaboration and Knowledge Sharing
At the heart of Python's success in cybersecurity lies its vibrant and collaborative community. With an abundance of online resources, forums, and tutorials, cybersecurity professionals can tap into a wealth of knowledge and expertise to enhance their Python skills and stay abreast of the latest industry trends. The spirit of collaboration within the Python community fosters innovation and continuous learning, driving advancements in cybersecurity practices and techniques.
6. Integrating Python with Security Tools and Platforms
Python's seamless integration with a wide array of security tools and platforms amplifies its impact in cybersecurity operations. Whether it's interfacing with network analysis tools like Wireshark, penetration testing frameworks like Metasploit, or threat intelligence platforms like MISP, Python's versatility enhances the functionality and effectiveness of these tools, enabling security professionals to combat threats more effectively.
7. Advancing Threat Detection with Machine Learning and AI
Python's support for machine learning and artificial intelligence (AI) opens up new frontiers in threat detection and cybersecurity analytics. By harnessing libraries such as TensorFlow, scikit-learn, and PyTorch, cybersecurity professionals can develop sophisticated models for anomaly detection, behavioral analysis, and predictive threat intelligence. These advanced capabilities empower organizations to proactively identify and mitigate emerging threats in real-time.
8. Securing Web Applications with Python Frameworks
Python's web frameworks, including Django and Flask, play a vital role in securing modern web applications against a wide range of cyber threats. With built-in security features, such as cross-site request forgery (CSRF) protection and input validation, Python frameworks provide a solid foundation for building resilient and secure web applications. Additionally, active community support and regular updates ensure that Python frameworks remain at the forefront of web application security practices.
Conclusion: Embracing Python's Potential for Cybersecurity Excellence
In conclusion, Python's versatility, robust library ecosystem, and scripting capabilities position it as a cornerstone of modern cybersecurity operations. From automating routine tasks to developing advanced threat detection solutions, Python empowers cybersecurity professionals to tackle the most complex challenges with confidence and efficiency. By embracing Python's potential and leveraging its myriad features, organizations can strengthen their cybersecurity posture and stay ahead of evolving threats in an increasingly digital world.
0 notes
Text
No updates to the app today, not that I didn't work on it. I was even too grumpy for video games. It was not a good day. I ate pizza even though I know I'm allergic. It's like would it be better to occasionally have a pizza and it hurts myself. IDK I feel like I can't control myself. I have an idea for a soap thing but it's like that not very vertically integrated of you. I'm leaning more towards using GraphQL instead of a REST API, just for ease of use. I tried the like I browser dev environment that was suggested from the remix tutorial. I made sure the instances were stopped, it was a pretty frustrating user experience, I don't remember what it was called git or but something. But I'll try the whole thing again in there. It's like 50 free hours / month if you link LinkedIn and if it can get me past the issue I was having with Prisma. When I did look at the Prisma documentation it seems like you need a database set up to use it and I don't have a database set up, unless there is one already there in the automation of the tutorial that I didn't see. As far as dev environments I think I can do just fine in a multipass or on my windows box. The other thing I've been doing for my birthday is binge watching HR pufnstuf (it's on the internet archive) it's been on my mind since I started using metasploit's LESTER (Local Exploit SuggesTER) on Kali for some hack the back stuff. It was the first thing I thought of, one of the doors in Wilhelmina Whack Witchiepoo's living castles is named Lester. As an adult I can see why people consider it to be cursed media but still mid key obsession with it. Like this is before googly eyes were widely available. The scale and scope of the production is bizarre. I'm still confused why it's hasn't had a reboot, particularly since that's where those stupid McDonald's characters are from. But while it it cursed and obscure, like couldn't find name of the talking door, had to go watch it, it kinda just makes me miss working with puppets. No not like chef and ansible, I used to make and performing with puppets. I thought they were going to be a large part of my life but I guess I was wrong about that. I guess it's just more reason to get back into animatronics. I'm going to go eat pizza now even though it's after 3 am on my birthday day and I have to be up in 6 hours.
1 note
·
View note
Text
Unleashing the Power of Kali Linux: A Comprehensive Guide
In the dynamic landscape of cybersecurity, it is crucial for organisations to stay ahead of evolving threats. In such an interconnected world where technology drives every aspect of our lives, the protection of sensitive information and digital assets has become a paramount concern. As we continue to embrace the digital revolution, the threat landscape for individuals, businesses, and governments has expanded exponentially. This is where the critical field of cybersecurity comes into play.
Cybersecurity, the practice of safeguarding digital systems, networks, and data from malicious attacks and unauthorized access, is a dynamic and ever-evolving discipline. From sophisticated cyber-espionage operations to relentless ransomware attacks, the adversaries seeking to exploit vulnerabilities are relentless and cunning. As the digital realm becomes increasingly integral to our daily existence, the need for robust and resilient cybersecurity measures has never been more pressing.To accomplish this, companies need to leverage robust tools and equip their professionals with cutting-edge knowledge. One such tool that has gained immense popularity among ethical hackers, penetration testers, and security enthusiasts is Kali Linux. In this blog post, we will delve into the essentials of Kali Linux, its features, and its significance in the realm of cybersecurity. Additionally, we will shed light on the Executive Programme in Cyber Security for Organisations (EPCSO) offered by IIM Indore, an esteemed program that equips professionals with the necessary skills to protect organisations from cyber threats.
Understanding Kali Linux:
Kali Linux, developed by Offensive Security, is a Debian-based Linux distribution designed for advanced penetration testing and digital forensics. It provides a comprehensive suite of tools that enable ethical hackers and security professionals to assess the security posture of systems, networks, and applications. Kali Linux offers a rich ecosystem of over 600 pre-installed tools, which are regularly updated to keep pace with emerging threats and vulnerabilities.
Features of Kali Linux:
Vast Toolset: Kali Linux boasts an extensive array of tools, including those for reconnaissance, vulnerability analysis, wireless attacks, password cracking, and more. Popular tools such as Nmap, Wireshark, Metasploit, and Aircrack-ng are pre-installed, making it a one-stop solution for security professionals.
Customization: Kali Linux allows users to customize their installations by choosing specific tools or categories during the installation process. This flexibility ensures that users can tailor the distribution to their specific requirements, optimizing their workflow and efficiency. The customization feature empowers cybersecurity professionals and enthusiasts to craft their specialized work environments. By handpicking the essential tools and tool categories during installation, users can optimize their workflows and improve resource management.
Forensics Capabilities: Kali Linux is renowned for its powerful forensics tools. It provides robust features for digital forensics and incident response, making it an indispensable resource for organizations dealing with cybercrime investigations and data recovery.
Community Support: Kali Linux has a large and active community of users and developers who collaborate, contribute, and provide support through forums, documentation, and tutorials. This thriving community enhances the accessibility of the tool and enables users to troubleshoot issues effectively.
Kali Linux in Cybersecurity:
Penetration Testing: Kali Linux serves as an invaluable tool for conducting penetration tests. Its comprehensive suite of tools allows professionals to identify vulnerabilities, exploit them, and provide recommendations to strengthen the security of systems and networks.
Ethical Hacking: Kali Linux facilitates ethical hacking by enabling security professionals to simulate real-world attacks, test defenses, and identify potential weaknesses. This proactive approach helps organizations fortify their security posture and stay one step ahead of malicious actors.
Education and Training: Kali Linux is widely used in cybersecurity education and training programs. Its user-friendly interface, extensive documentation, and wealth of learning resources make it an ideal platform for aspiring security professionals to gain hands-on experience in various domains of cybersecurity.
IIM Indore's Executive Programme in Cyber Security for Organizations (EPCSO):
IIM Indore, one of India's premier management institutions, offers the Executive Programme in Cyber Security for Organizations (EPCSO) to equip professionals with the necessary skills to navigate the complex world of cybersecurity. This program caters to mid to senior-level executives, managers, and leaders responsible for safeguarding their organizations from cyber threats.
EPCSO covers a wide range of topics, including cyber threat landscape analysis, risk management, incident response, digital forensics, ethical hacking, and emerging trends in cybersecurity. The curriculum is designed to provide participants with a holistic understanding of cybersecurity and its implications for organizations.
Eradicate cybersecurity threats by upskilling from IIM Indore in collaboration with Jaro Education. Get in touch with us to know more about the programme.
0 notes
Text

Finding vulnerabilities with Metasploit http://dlvr.it/RrxXSd
0 notes
Text

What is Metasploit ? A complete guide for beginners on Metasploit software. What is it ? Why hackers use it. Everything in detail.
#blogger#blogging#blog#facts#hacking#metasploit#hackers#ethical hacking#white hat#black hat#coding#c++ for beginners#c++ language#c++ programming#c++ tutorial#c++#python
0 notes
Text
Finding Open Ports with Nmap
When traffic is sent to a computer, it is sent to a certain port. This port depends on the software sending/receiving the traffic. This ensures that the data is sent to the software that needs it, for example websites normally operate on port 80 or 443 (depending on if the site uses HTTP or HTTPS respectively), whereas SSH uses port 22. You can read more on ports here.
Nmap is a tool which allows hackers or network administrators to tell which ports are open on a device. This information can be used to find vulnerable services to exploit, or to find services which shouldn’t be running and which a hacker or malware may have added.
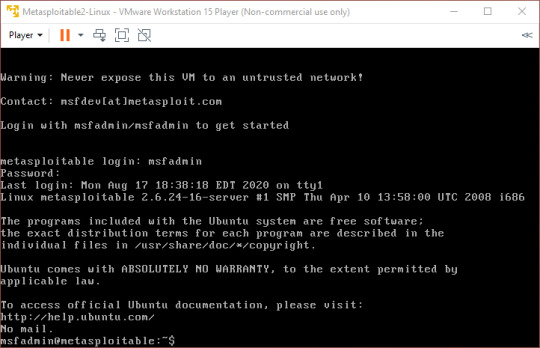
The official site for nmap is here, and it can be downloaded from there, however it comes packaged with Kali. I will be scanning a VM running metasploitable, which is an OS created by the creators of metasploit (a hacking tool, but more on that another day) and is intentionally vulnerable. I will be using this machine in many of my tutorials to demonstrate techniques/attacks. Creating a Metasploitable VM is identical to creating a Kali box, but using a Metasploitable image instead.
After booting up the Metasploitable machine, we see something like this:
We can then run the command ‘ip route’ to find our local IP address.
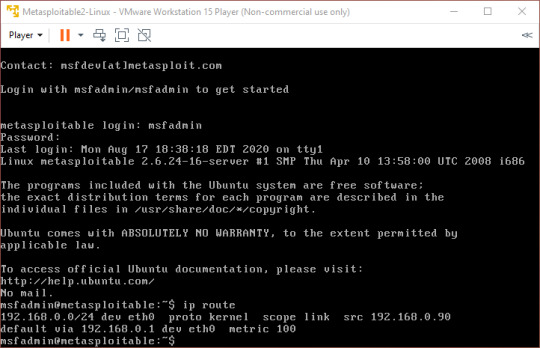
Quite a lot is shown, but what we are looking for is the address after ‘src’. This tells me that my local IP address is 192.168.0.90.
Without closing Metasploitable, we open our Kali VM as well and log in. to check that we can connect to Metasploitable, we will ping the address we just found.
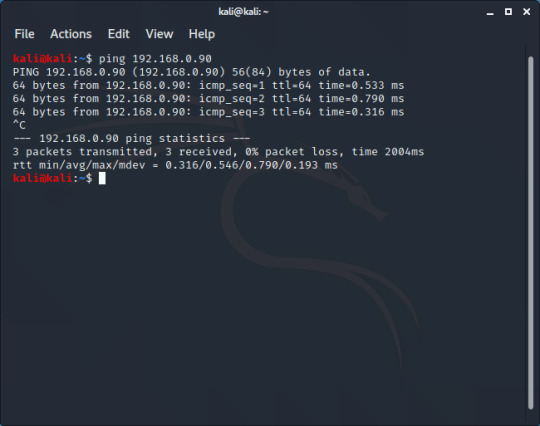
‘64 bytes from 192.168.0.90′ tells me that I am getting a response from Metasploitable. Let’s start an nmap scan.
We are going to start with just a simple scan. I will type ‘nmap 192.168.0.90′ without any other flags.
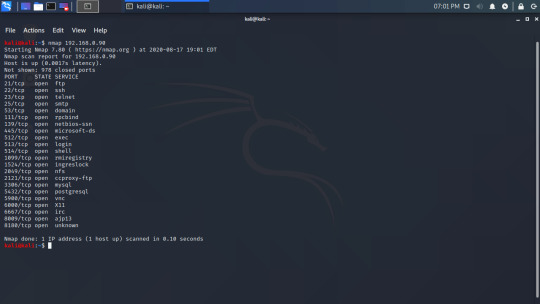
Here we can see that there are 21 ports running. Knowing what ports are open is useful, but we can find more information. Let’s find the OS with the -O flag (bear in mind that this requires sudo)
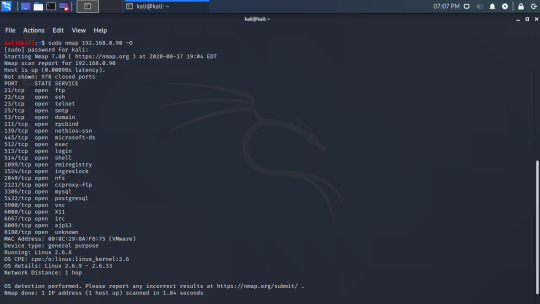
Along with the same information from before, we now have more information. We now know the MAC address, the OS it is running (Linux 2.6), and some more information about the OS.
Nmap can also tell us (a guess) about the software running on each port with the -sV argument.
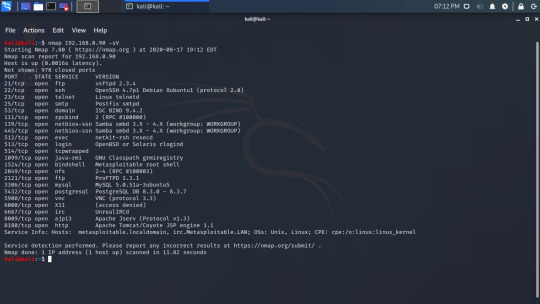
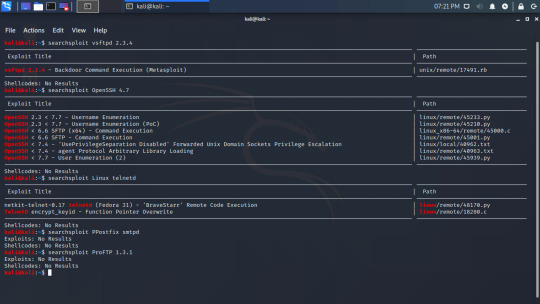
We can use this software version to search for exploits, and I will write another guide on that soon but here is a quick example of just some of the exploits.
Using the -h flag with nmap will output all of the available options:
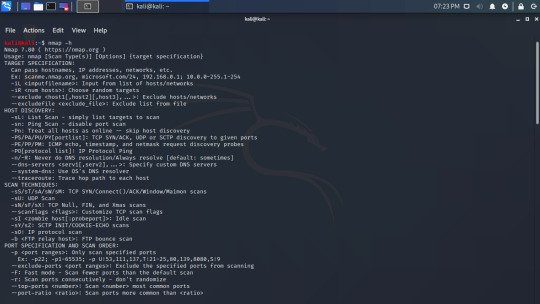
As you can see, there are a lot of options. I recommend using a site like HackTheBox or TryHackMe to give you a place to practice (I have found TryHackMe is better for beginners), or you can practice with a Metasploitable box.
Nmap is a very useful tool and enables you to find so much information. It is worth learning well and I haven’t begun to scratch the surface of all the functionality.
1 note
·
View note
Text
MeterSSH – Meterpreter over SSH
MeterSSH is a way to take shellcode, inject it into memory then tunnel whatever port you want to over SSH to mask any type of communications as a normal SSH connection. The way it works is by injecting shellcode into memory, then wrapping a port spawned (meterpreter in this case) by the shellcode over SSH back to the attacker’s machine. Then connecting with meterpreter’s listener to localhost…
View On WordPress
#autossh#backtrack#backtrack (operating system)#backtrack 5#clientalivemaxcount#hack#hacker (fictional job title)#hacking#hacking class#hacking tutorial#hacking video#kali#kali linux#kali linux 2017.1#keepalive#linux#metasploit#metasploit project (software)#metasploit tutorial#meterpreter#modules#msf#msfconsole#nat#nat traversal#network address translation#penetration testing#pentest#pentesting#persistent ssh
0 notes
Text
Unleashing the World of Ethical Hacking and Penetration Testing: A Beginner’s Guide
In today’s digital landscape, where cybersecurity threats loom large, ethical hacking and penetration testing have emerged as critical skills for safeguarding systems and networks. If you aspire to become an ethical hacker or penetration tester, this comprehensive guide will walk you through the steps to embark on this exciting journey.
Let’s learn into some of the best ones, with a particular highlight on the unique ethical hacking course available at ACTE Technologies in Bangalore.

Some Step-By-Step Guide To Get You Started:
Step 1: Build a Strong Foundation: Start by acquiring a solid understanding of computer networks, operating systems, and programming languages. Familiarize yourself with TCP/IP protocols, network architecture, and key security concepts. Online courses, tutorials, and books on networking and security fundamentals will serve as valuable resources.
Step 2: Master Security and Vulnerabilities: Develop a deep knowledge of different security vulnerabilities, such as web application flaws (e.g., SQL injection, cross-site scripting), network vulnerabilities (e.g., misconfigurations, weak passwords), and operating system weaknesses. Study common attack vectors, encryption methods, cryptography principles, and security best practices.
Step 3: Explore Ethical Hacking Tools and Frameworks: Get acquainted with popular ethical hacking tools and frameworks like Kali Linux, Metasploit, Burp Suite, Nmap, Wireshark, and OWASP ZAP. Understand their functionalities and learn how to leverage them effectively for reconnaissance, scanning, exploitation, and vulnerability assessment.
Step 5: Embrace Hands-on Practice in a Safe Environment: Set up a virtual lab environment using virtualization software such as VirtualBox or VMware. This allows you to create isolated networks and systems for practicing without causing harm to real-world systems. Engage in hands-on activities like network scanning, vulnerability exploitation, privilege escalation, and post-exploitation tasks.
Step 6: Challenge Yourself with Capture the Flag (CTF) Competitions: Participate in Capture the Flag challenges, which simulate real-world cybersecurity scenarios and test your skills in various hacking and penetration testing areas. Websites like HackTheBox, TryHackMe, and OverTheWire offer CTF challenges suitable for beginners to advanced participants. These challenges provide invaluable practical experience and foster problem-solving abilities.
Step 7: Stay Abreast of the Latest Trends and Engage in the Community: Keep up with the ever-evolving field of cybersecurity by following reputable blogs, forums, and social media accounts. Stay informed about the latest security vulnerabilities, tools, and techniques. Engage with the cybersecurity community by attending conferences, joining online forums, and participating in discussions. Networking with professionals in the field can provide valuable insights and opportunities for growth.
Step 8: Embrace an Ethical Mindset: Approach ethical hacking and penetration testing with a strong ethical mindset. Always obtain proper authorization before conducting any security assessments or penetration tests. Respect privacy, confidentiality, and legal boundaries. Ethical hackers and penetration testers have a responsibility to protect systems and data while adhering to ethical guidelines.
Embarking on the path of ethical hacking and penetration testing requires a combination of theoretical knowledge, practical skills, and an unwavering commitment to ethical conduct.
By following the steps outlined in this guide, you can lay a strong foundation, acquire the necessary skills, and navigate the dynamic field of cybersecurity with integrity. Remember, continuous learning, hands-on practice, and ethical responsibility are the cornerstones of a successful ethical hacker or penetration tester.
To learn more considering a top software training institute can provide certifications, job opportunities, and experienced guidance, available both online and offline. Experienced teachers can help you learn better. Take it step by step and consider enrolling for a better understanding.
0 notes
Text
Hacking Tutorials

Step-by-Step Hacking Tutorials about WiFi hacking, Kali Linux, Metasploit, exploits, ethical hacking, information security, malware analysis and scanning Read more…
1 note
·
View note
Text
Week 7 Evening Lecture
PSA
Something Awesome is due TOMORROW before the evening lecture
MAJOR YIKES
Presentation: Bug Bounties
Started off with a Kahoot which was kind of strange. I was coming first, but the last question tripped me up. I thought we simply send them an email like Richard alluded to in the morning lecture, but apparently we should make a report and submit it. It was really unexpected I guess because they tested us before even doing the presentation (kinda counter-intuitive).
Anyway it was a nice and simple presentation that covered a few of the basics with getting started being a bug hunter. The example they showed was on a real website (HackerOne), where big companies like Tesla posted their applications for hackers to test and find bugs. It was good since they outlined the key features of the spec.
For example, Tesla clearly outlines specific things that they do not want reported like Social Engineering attacks, phishing, etc. In addition, there is information about the payouts they give and what kind of information (source code, etc) they provide to start finding bugs. All these things were considered ‘in scope’ meaning that there were specific things they wanted people to be looking at. However, there were also other things that they outlined as ‘out of scope’ so that hackers wouldn’t waste their time looking at other things.
Getting Started Tips
Learn web application principles
Look for assets that have changed recently; Reddit /r/tesla posts the software updates and patch notes (find bugs there)
Look for publicly disclosed reports
Fuzzing (covered by @theslazarus) Fuzzing is a useful bug testing process in which you can run automated tests that cover a range of possible cases. This is a lot more streamlined than manual testing and writing your own cases, because this generates all the possible inputs and interactions a user could use with your software and allows you to analyse it for any unexpected behaviour.

Fuzzers come in all different shapes and sizes, but generally fall into two main categories:
Mutation-based
Generation-based
We can use fuzzers to trace different types of bugs. In the example, @theslazarus showed how he used a fuzzer to test for heartbleed in different C programs. A good tip he gave was to follow tutorials online on how to utilise these and go on Github and test other people’s programs to see what bugs they have.
Crapple Bug (How to get root on a Mac) So apparently as your Mac is starting up, if you hold down Apple + S, you are able to get root access into the system. This occurs if you HAVEN’T ENCRYPTED YOUR HARD DISK but it’s strange as to why this is even a thing in the first place. However it does go to show that once someone gains access to the hardware, they have access to EVERYTHING.
Presentation: Pen Testing
Pen testing is an authorised simulation attack usually done in a sandbox to evaluate certain security risks. It is usually performed for companies in order to identify vulnerabilities and strengths that exist in their infrastructure.
For example, if you sent a ninja to break into your own house.
The ninja is the pen-tester
Your house is the system
Stages of Pen Testing
Recon
Planning
Exploitation
Post-Exploitation
Establish persistence
Establishing persistence I think is a really critical point. A hacker may break into your system at one point but remain dormant for a long period of time, or create some way to get back in (backdoor). This way they can plan certain attacks once they know they have access and execute this easily.
Demonstration The demonstration was quite nice where the presenters utilised Kali (gives you root access to everything) and hacker tools like Metasploit and Gobuster to analyse and brute force into servers. They attacked a system they set up on Wordpress and tried to login into ‘admin’. Although the password they entered was wrong, Wordpress indicated that the password for ‘admin’ was incorrect, giving out the information that there actually was an administrative account called ‘admin’. Lo and behold, the password to that account was indeed admin. For establishing persistence, the demonstrator installed a plugin he wrote himself that allowed him to create a shell and get back into the server (shell scripting).
Kahoot Was an interesting kahoot. I won which was cool got a s/o from Bucky.
Back2Lecture: Homework
Richard gave us more homework to do ahhhhhhhhh. It’s not compulsory, but I am interested in these things and do want to research them but I’m so busy and it just keeps piling on and on there’s so much stuff he wants us to do and then it’ll be assessable just you wait. Anyway here’s what he wants us to look up (it’s in the notes; https://www.openlearning.com/courses/securityengineering19t2/notes/slides07/)
Find out about current state of biometrics
Read about transport for NSW idea of using Facial Recognition rather than opal cards (case study)
Read about san fransisco ban on biometrics
Read about University research allegedly helping Chinese security forces to track and detain Uyghur citizens in Xinjian, China
Think about ways you can use facial recognition (China)
Diffie-Hellman does not give Authentication
One thing to note about Diffie-Hellman is that it’s NOT giving us AUTHENTICATION, because we aren’t verifying the identity of who we’re communicating with. DH only guarantees that only the parties have the shared secret (the key) which is CONFIDENTIALITY. So even if you are doing a key-exchange with someone across the world, you don’t actually know if it is the person who says they are who they say they are lol.
Blind Computers
Drawing back from last week’s lecture, Richard reminded us how Computers are just like someone who lives in a dark jail cell, separate from the real world. A computer doesn’t “understand context” or “identify things” the way that humans do. Computers are machines that are simply processing 1s and 0s.
Computers don’t understand things like we do. If you asked it to verify the identity of someone through a photo, it would simply be taking that image’s binary encoding and doing a bit-wise comparison. So in the instance that a it can do a comparison accurately, it is because the computer is PRE-LOADED with that information. It can only do a comparison if it has something it compare the input with. In this case, the pre-loaded information would be the stored binary information of a picture of the person’s face. However even with that, and no connection to the outside world, the computer still has to make a decision whether or not that person is who they say they are. And that decision is VERY HARD with what they understand and what they’re given. In the end, it comes down to the shared secret that is helping them make that decision.
3 notes
·
View notes
Text
Ispy - Eternalblue / Bluekeep Scanner And Exploiter
Ispy - Eternalblue (MS17-010) / Bluekeep (CVE-2019-0708) Scanner And Exploit #automation #Bluekeep #CVE20190708
[sc name=”ad_1″]
ispy : Eternalblue(ms17-010)/Bluekeep(CVE-2019-0708) Scanner and exploiter ( Metasploit automation )
How to install :
git clone https://github.com/Cyb0r9/ispy.git cd ispy chmod +x setup.sh ./setup.sh
Screenshots :
Tested On :
Parrot OS
Kali linux
Tutorial ( How to use ispy )
info
GitHub profile : https…
View On WordPress
1 note
·
View note
Text
Kali Linux
Kali Linux, the user-friendly and powerful open-source operating system from Offensive Security, is a popular Linux-based platform for security and penetration testing. This Debian-based system is designed for advanced users seeking to secure and evaluate their IT networks.
Kali Linux comes with a feature-rich set of tools and applications to optimize system performance. For example, it includes Metasploit, which allows security and network penetration testing, as well as Burp Suite, which helps users detect web vulnerabilities. The OS also includes many of the same security tools used by professionals such as password crackers, sniffers, and Wireless Attack tools. This powerful collection of applications covers every aspect of network security, from low-level hardware analysis to ethical hacking and digital forensics.
Another advantage of using Kali Linux is that it is highly customizable. Unlike other versions of Linux, Kali Linux allows users to tailor the OS according to their individual needs and objectives. Aside from core features and applications, the OS also provides an extensive set of packages that can help expand its ability, such as Kali Menu, a feature that enables smooth OS navigation and integration with other systems.
Kali Linux is also an excellent platform for educational purposes. It includes detailed tutorials and explanations of the various tools and techniques used in network security. The OS also includes many resources such as textbooks, research papers, and computer security lectures. This means that users don’t have to guess or search the web to find answers to their security-related questions.
Finally, Kali Linux is highly compatible and can be run on a variety of devices, from bare-metal systems to virtual machines and cloud-based systems. This makes it ideal for situations when users need to quickly spin up a secure environment for their applications and work.
In short, Kali Linux is a powerful and user-friendly security platform. Its comprehensive set of applications, customizability, educational resources, and compatibility make it an ideal choice for security and penetration testing.
For more information visit this website Thedigishastra
For more information visit this page kali linux
0 notes
Text
IS PYTHON IMPORTANT FOR HACKING?
Yes, Python is an important language in the field of cybersecurity and hacking. It is used for tasks such as automation, data analysis, web application security, and exploit development. The versatility and ease of use of Python make it a popular choice among cybersecurity professionals.
Additionally, Python has numerous libraries and modules specifically designed for security purposes, such as Scapy, Requests, and Paramiko. These tools provide functionality for network scanning, packet analysis, and SSH connection, among others. Many open-source cybersecurity tools are written in Python, making it easier for security experts to modify and customize existing tools to meet their specific needs. Overall, Python is a valuable language in the cybersecurity field.
Python's importance in hacking lies in its versatility and ease of use. It is a popular choice for automating repetitive tasks, writing scripts for data analysis, and developing exploits. The language's simplicity and readability make it a good choice for beginners, while its wide range of libraries and modules provide advanced capabilities for more experienced hackers. Additionally, many popular hacking tools and frameworks, such as Metasploit, are written in Python, allowing for customization and integration with other tools. In short, Python is an important language for hackers due to its versatility, ease of use, and support for cybersecurity tasks.
In addition to the reasons mentioned earlier, Python also provides support for a variety of platforms and operating systems, making it a versatile tool for hackers. The language also has a large community and many resources available, such as tutorials, documentation, and forums, which can help hackers improve their skills and stay up-to-date with the latest trends and technologies. Python is also suitable for creating cross-platform tools and for interacting with APIs, making it a valuable tool for reconnaissance and information gathering tasks. In conclusion, Python's versatility, ease of use, support for various platforms, and strong community make it a valuable language for hackers.
Lastly, Python’s high-level programming features, such as dynamically-typed variables and automatic memory management, can greatly simplify and speed up the development of hacking tools. Python also allows for easy integration with other programming languages, making it possible to write code that leverages the strengths of multiple languages and tools. This makes Python a valuable language for creating custom and complex hacking tools that meet the specific needs of individual hackers or organizations.
To summarize, Python is an important language in the field of hacking due to its versatility, ease of use, strong community, support for various platforms, and its high-level programming features that simplify and speed up the development of hacking tools.
It's worth mentioning that while Python can be a valuable tool for both defensive and offensive security, it's important to use it ethically and within the bounds of the law. Python's capabilities can be used for malicious purposes if not used responsibly. It's also important to stay informed about current trends, best practices, and ethical guidelines in the cybersecurity industry.
In conclusion, Python's versatility, ease of use, strong community, and support for various platforms make it a valuable language for both defensive and offensive cybersecurity tasks, but it's important to use it responsibly and stay informed about ethical guidelines and best practices in the industry.
0 notes